How Does a Firewall Work?
In this tutorial, we are going to see how does a firewall work?
Any computer connected to the Internet is susceptible to a hacker attack. The most common way for a hacker to attack a computer is to scan the network (by sending packets of data at random) for a connected machine and then look for a security hole to exploit and access the data on it.
This threat is even greater if the machine is permanently connected to the Internet for several reasons:
- The target machine is likely to be connected without being monitored;
- The target machine is usually connected with a larger bandwidth;
- The target machine does not change its IP address (or not much).
So, it is necessary, both for company networks and for Internet users with a cable or ADSL connection, to protect themselves from network intrusions by installing a protection device.
What is a Firewall?
A firewall is a system that protects a computer or a network of computers from intrusions from a third-party network (especially the Internet). The firewall is a system that filters data packets sent to and from the network. It is a filtering gateway with at least the following network interfaces:
- an interface for the network to be protected (internal network);
- an interface for the external network.
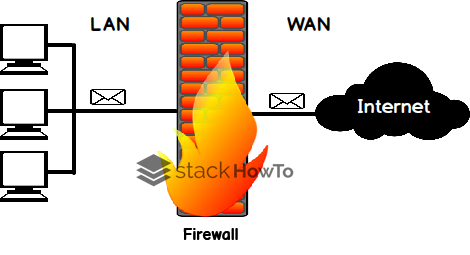
The firewall system is a software system, sometimes based on dedicated network hardware, which acts as an intermediary between the local network (or the local machine) and one or more external networks. It is possible to put a firewall system on any machine and with any system as long as :
- The machine is powerful enough to handle the traffic;
- The system is secure;
- No other service than the packet filtering service is running on the server.
How Does a Firewall Work?
A firewall system contains a set of predefined rules allowing:
- Authorize the connection (allow);
- Block the connection (deny);
- Reject the connection request without notifying the sender (drop).
All these rules allow to implement a filtering method depending on the security policy adopted by the entity. We usually distinguish two types of security policies:
- allow only those communications that have been explicitly authorized
- or to prevent communications that have been explicitly denied.
The first method is undoubtedly the most secure, but it imposes a precise and restrictive definition regarding communication needs.
What are the 3 types of firewalls?
- Static Filtering
- Dynamic Filtering
- Application Filtering
Static Filtering
A firewall system works on the principle of stateless packet filtering. It analyzes the headers of each data packet (datagram) exchanged between an internal network machine and an external machine.
Thus, the data packets exchanged between a machine on the external network and a machine on the internal network pass through the firewall and have the following headers, which are systematically analyzed by the firewall:
- IP address of the sending machine;
- IP address of the receiving machine;
- type of packet (TCP, UDP, etc.);
- port number (remember: a port is a number associated with a service or a network application).
The IP addresses found in packets identify the sending machine and the target machine, while the packet type and port number give an idea of the type of service used.
The following table gives some examples of firewall rules:
| 1 | Accept | 192.168.1.34/24 | 193.200.2.56 | tcp | Any | 80 |
| 2 | Deny | 192.168.1.55 | Any | tcp | Any | 80 |
| 3 | Accept | Any | 193.200.2.86 | udp | Any | 23 |
| 4 | Deny | Any | Any | Any | Any | 25 |
The recognized ports (with numbers between 0 and 1023) are associated with common services (for example, ports 25 and 110 are associated with e-mail, and port 80 with the Web). At a very basic level, most firewall devices are configured to filter communications by port. It is generally advisable to block all ports that are not required (depending on the security policy).
For example, port 23 is often blocked by default by firewall devices because it corresponds to the Telnet protocol, which is used to emulate terminal access to a remote machine so that commands can be executed remotely. The data exchanged by Telnet is not encrypted, which means that someone can easily listen in on the network and steal any passwords that may be circulating in cleartext. Administrators generally prefer the SSH protocol, which is considered secure and provides the same functionality as Telnet.
Dynamic Filtering
The static packet filtering only examines IP packets independently of each other, which corresponds to level 3 of the OSI model. However, most connections are based on the TCP protocol, which manages the notion of session, in order to ensure the smooth running of communications. On the other hand, many services (FTP, for example) initiate a connection on a static port but open a port dynamically (i.e., randomly) in order to establish a session between the server machine and the client machine.
Thus, it is impossible with static packet filtering to predict which ports to allow or disallow. To solve this problem, the dynamic packet filtering system is based on the detection of layers 3 and 4 of the OSI model, allowing to monitor the transactions between the client and the server, and this is called “stateful inspection” or “stateful packet filtering”.
Application Filtering
Application filtering allows filtering communications by application. Application filtering, therefore, operates at level 7 (application layer) of the OSI model, unlike simple packet filtering (level 4). Application filtering, therefore, requires knowledge of the protocols used by each application.
A firewall performing application filtering is generally called an “application gateway” (or “proxy”), because it acts as a relay between two networks by intervening and performing a fine-grained validation of the content of packets sent. The proxy, therefore, represents an intermediary between the machines on the internal network and the external network, undergoing the attacks in their place. Moreover, application filtering allows the cancellation of the headers preceding the application message, which provides an additional level of security.
The limits of firewalls:
A firewall system does not offer absolute security. Firewalls only offer protection if all communications to the outside world systematically pass through them and if they are correctly configured. Thus, access to the external network by bypassing the firewall is a security flaw. This is particularly the case for connections made from the internal network using a modem or any other connection method that is not controlled by the firewall.
Similarly, the insertion of external storage media on internal network machines or laptops can seriously affect the overall security policy.
Finally, in order to guarantee a maximum level of protection, it is necessary to monitor the firewall’s activity log in order to be able to detect intrusion attempts and anomalies. In addition, it is recommended to keep a security watch (by subscribing to CERT security alerts, for example) in order to modify the settings of your device according to the publication of alerts.
The installation of a firewall must therefore be done in accordance with a real security policy.