What is a Digital Signature in Cryptography?
In this tutorial, we are going to see What is a Digital Signature in Cryptography?
The digital signature paradigm is a process that guarantees the authenticity of the sender (authentication function) and verifies the integrity of the message received.
The digital signature also provides a non-repudiation function, which means that it ensures that the sender has sent the message ( meaning that it prevents the sender from denying having sent the message).
What is a hash function?
A hash function (sometimes called a condensation function) is a function that allows getting a condensed text (also called condensate or hash or message digest), which means a short sequence of characters representing the text it condenses. The hash function must be designed in such a way that it associates one and only one hash with a plain text (this means that the slightest modification of the document leads to the modification of its hash). On the other hand, it must be a one-way function so that it is impossible to retrieve the original message from the hash. If there is a way to retrieve the plaintext message from the hash, the hash function is said to be “secretly breached”.
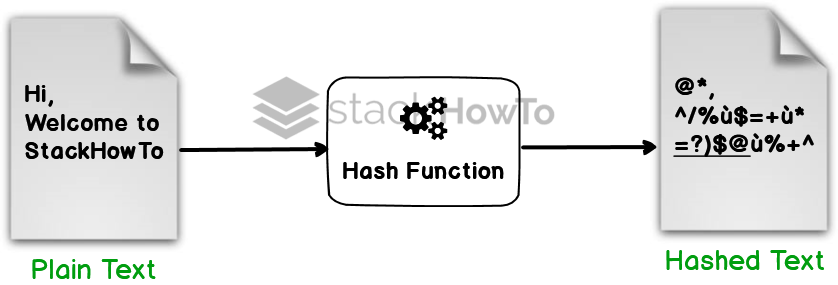
Thus, the hash represents the fingerprint of the document.
The most commonly used hash algorithms today are :
- MD5 (MD standing for Message Digest): Developed by Rivest in 1991, MD5 creates a 128-bit fingerprint from the arbitrary-sized text by processing it in blocks of 512 bits. It is common to see documents downloaded from the Internet accompanied by an MD5 file. This is a hash of the document that allows the integrity of the document to be verified)
- SHA (for Secure Hash Algorithm) creates 160-bit long fingerprints
- SHA-1 is an improved version of SHA dating from 1994 and producing a 160-bit fingerprint from a message with a maximum length of 264 bits by processing it in blocks of 512 bits.
Integrity verification:
By sending a message with its hash, it is possible to guarantee the integrity of a message, which means that the recipient can verify that the message has not been altered (intentionally or by accident) during the communication.
When the message is received, the recipient simply calculates the hash of the received message and compares it with the hash attached to the document. If the message (or the hash) has been altered during the communication, the two fingerprints will not match.

Image source: https://commons.wikimedia.org/wiki/File:Digital_Signature_diagram.svg
The use of a hash function can verify that the hash matches the message received, but there is no proof that the message was actually sent by the person believed to be the sender.
Thus, to guarantee the authentication of the message, the sender only has to encrypt (usually called sign) the hash with his private key (the signed hash is called certificate) and send the certificate to the recipient.
When the message is received, the recipient simply decrypts the certificate with the sender’s public key, then compares the hash obtained with the hash function to the hash received as an attachment.