What is Transposition Cipher With Example?
In this tutorial, we are going to see What is transposition cipher with example?
A transposition cipher consists in changing the order of the letters, thus building anagrams. This method has been known since antiquity since the Spartans already used a Scytale.

Image source: https://commons.wikimedia.org/wiki/File:Skytale.png
A statistical analysis of transposition ciphers is not useful, since only the order of the symbols is different; the symbols remain the same. Thus, the most frequent symbols in the clear message will obviously remain the most frequent in the encrypted message.
For very short messages, such as a simple word, this method is not very secure because there are few variants for redistributing a handful of letters. For example, a word of three letters can only be turned into 6 (=3!) different positions. So “how” can only be turned into “woh”, “who”, “hwo”, “owh”, “ohw” or “how”. Of course, when the number of letters increases, the number of arrangements increases rapidly and it becomes almost impossible to find the original text without knowing the scrambling process.
Rectangular transpositions:
To perform a cipher by rectangular transposition, we start by agreeing on a keyword. Let’s choose for our example the word HELLO. We then classify the letters of the word HELLO in alphabetical order, and we assign to each letter its number in alphabetical order. Thus, we give H the number 8, E the number 5, the first L the number 12, the second L the number 13, the O the number 15, etc…
Then we create a table as follows:
- the first line consists of the key letters;
- the second line is made up of the associated numbers;
- the table is then completed by filling it with letters from the message to be encrypted. We write on each line as many letters as there are letters in the key. Sometimes, the last line is not complete.
For example, if we want to calculate Welcome to StackHowTo, the table we build is the following:
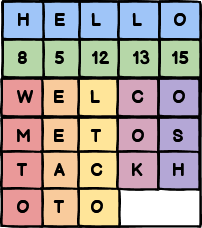
Then, we write the content of column 1, then the content of column 2, etc… The encrypted message we get is then :
WMTO EEAT LTCO COK OSH